Industries We Serve
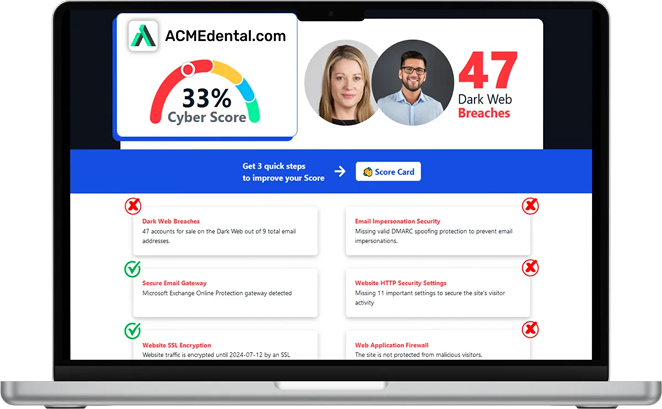
Your comprehensive CYBER Security score – Get it Now
Search the dark web, website and stolen passwords in 60 seconds...
We’re in the Business of
Resolving Issues Fast, Ensuring Compliance
And Setting Your Entire Company Up for Success
Welcome to

We Resolve Most Issues Remotely in Under 10 Minutes
See firsthand how our IT services resolve most issues remotely in under 10 minutes, and deliver on-site help within 4 hours - in Florida and across the U.S.
Stop struggling with slow IT. Get the help you need, when you need it.
Call (561) 786-2166 or email us [email protected].
What Security-First IT Is

Proactive Risk Detection
Stop threats before damage occurs with layered monitoring, real-time alerts, and compliance oversight in place.

Audit-Ready Systems
Maintain HIPAA, SEC, and CMMC readiness with documentation, reporting, and proactive remediation plans always.

Remote Threat Response
Get fast incident resolution from experts who fix issues in minutes before they impact business operations fully.
What Security-First IT Isn’t

Delayed Threat Discovery
Without layered visibility, threats go unnoticed until damage is done and recovery becomes harder and slower.

Unprepared for Audits
Missing documentation and poor system hygiene increase audit failures, fines, and regulatory violations repeatedly.

Slow or Absent Response
Threats linger when providers delay, ignore alerts, or lack urgency, escalating damage and downtime dramatically.
Our Managed IT Services

Cybersecurity
We secure your systems with layered protections, compliance alignment, and real-time response to stop threats.

vCIO/vCISO
We guide your IT strategy, compliance audits, and long-term planning with leadership tailored to your specific business needs.

Cloud Solutions
We streamline and secure your Microsoft 365 environment to reduce app sprawl, improve access, and control costs.

VoIP Phones
We monitor, support, and resolve issues fast with guaranteed response times that keep your business moving forward.
Tired of IT Headaches? Get Support That Actually Works
What Clients Say About Us
How Will Our IT Services Make Your Business Better?

Stronger Security, Simpler Systems, Faster Support
Our IT services eliminate downtime, protect sensitive data, and reduce tech waste by aligning tools, strategy, and compliance under one responsive, accountable team that solves problems fast. We simplify IT management, close security gaps, and consolidate redundant platforms to improve performance, cut costs, and meet regulatory demands.
Not Convinced? That's OK — Get to Know Us Through Our Monthly Email Tips
We get it—you don’t trust just any IT company. That’s why we let our expertise speak for itself. Sign up for our monthly newsletter and see how we cut through the noise to deliver real IT solutions. No fluff, no spam. Just useful, no-nonsense insights that you can actually use.

Experience fast & Local IT Support
See firsthand how our IT services resolve most issues remotely in under 10 minutes, and deliver on-site help within 4 hours.
Stop struggling with slow IT. Get the help you need, when you need it.
Call (561) 786-2166 or email us [email protected].
© Copyright 2026 Cloud Choice Technologies. All Rights Reserved. Built with MSP Sites. | Privacy Policy | Areas We Serve


























